Usually after pressing the "Power" on your PC, you will have enough time to brew a cup of coffee or tea due to the length of time it takes to boot your computer. Especially if your PC has a myriad of applications that are automatically lit, perhaps in addition to coffee, you can all shower and make breakfast first.
Without an increase in hardware performance are significant, it is not much you can do to speed up boot Windows. But there are ways to speed up the time needed by the desktop to achieve the condition "ready to work". Let's look at some way below, either use the capabilities already available and applications from the outside.
When you install a new application on your computer these days, not a few who immediately made him a startup program; to check whether an upgrade or just to remind users that the application has been installed as an icon in the lower right of the PC such as chat applications like Yahoo , MSN, Skype, etc.
The problem comes when you install many applications are rarely used, but they still appear on the startup process, it is consuming CPU cycles, memory and time. The easy way to handle it is to delete applications that do not use. Remove All Startup Item
While many programs that can clean startup applications, you really can do it manually without using additional applications.
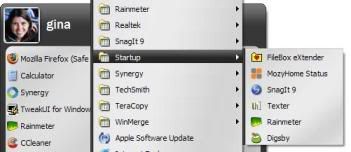
The best place, safest and most basic to start doing this is the program group "Startup" in the "Start Menu" Windows. Mouse to navigate the "Startup" and see what the program appears. Right-click on programs that do not need active at startup and select "delete".
While many programs that can clean startup applications, you really can do it manually without using additional applications.
The best place, safest and most basic to start doing this is the program group "Startup" in the "Start Menu" Windows. Mouse to navigate the "Startup" and see what the program appears. Right-click on programs that do not need active at startup and select "delete".
After doing this process, it comes out the ultimate style. Windows also can automatically activate the program from other places. Click the Start Menu, select "Run" then type "msconfig" and press [ENTER] to enter into the Windows system configuration functions. Move to the tab "Startup" to see a more comprehensive list of anything that came on automatically. Look below displays.
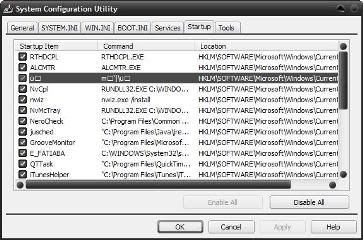
The list does look complicated and confusing. What is "ctfmon" or "RTHDCPL"? Column "command" which sometimes includes the location of the application, sometimes also can provide clues about the contents of the application. As usual, Google has always been your friend in situations like this.
From here you can remove the check mark on the application that you do not want to turn on the startup process. Do not remove the check mark on the application that you do not understand, begin the application that you know and not used. For example, if you're not a heavy user of iTunes or Quicktime, but the actual application on the PC installed to use sometimes, you can remove the check mark on "QTTask" and "iTunesHelper" and both these applications will no longer appear automatically when you restart the computer.
You can turn back the application by visiting the "msconfig" and do the above procedure again. Using "msconfig" it takes a little courage and knowledge of Windows users. But there are still other ways to do the same process using third-party applications and application cleaning. Download the Windows Optimization Program
Actually there are many other applications that have the ability to manage "startup", but let us look at two of the best course.
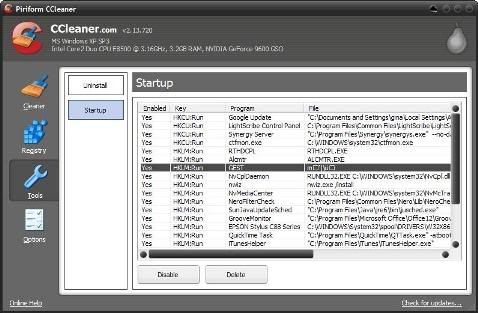
CCleaner (which stands for "Crap Cleaner") can check your system for many things and get rid of excess. Click the "Tools", then the "Startup" to achieve it. As you can see, this application offers more information than "msconfig" at the top and can help provide an explanation for existing programs. You can disable and remove everything from startup using these buttons.
From here you can remove the check mark on the application that you do not want to turn on the startup process. Do not remove the check mark on the application that you do not understand, begin the application that you know and not used. For example, if you're not a heavy user of iTunes or Quicktime, but the actual application on the PC installed to use sometimes, you can remove the check mark on "QTTask" and "iTunesHelper" and both these applications will no longer appear automatically when you restart the computer.
You can turn back the application by visiting the "msconfig" and do the above procedure again. Using "msconfig" it takes a little courage and knowledge of Windows users. But there are still other ways to do the same process using third-party applications and application cleaning. Download the Windows Optimization Program
Actually there are many other applications that have the ability to manage "startup", but let us look at two of the best course.
CCleaner (which stands for "Crap Cleaner") can check your system for many things and get rid of excess. Click the "Tools", then the "Startup" to achieve it. As you can see, this application offers more information than "msconfig" at the top and can help provide an explanation for existing programs. You can disable and remove everything from startup using these buttons.
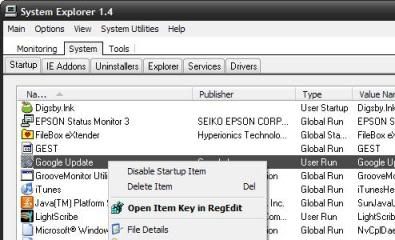
If you do not want to install other software to clean your system, System Explorer comes in a portable version with a "startup manager" feature-rich, complete with the registry, viruses and online talker even a Google search for the file name. On the tab "system", click the tab "startup" to see what came on automatically on your PC. Here is a look.
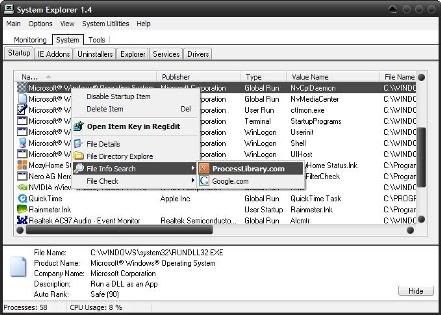
As you see, just right-click, you can directly to the registry editor or do a search on Google ProcessLibrary.com or for an application. In addition, the program maker and the file path is also included, offering more information about an application and what you can do to turn it off.
Ccleaner and SystemExplorer addition, there's more like alternati MZ Ultimate Tweaker and RegToy. Defer Application Startup Process
Surely not just one program only result in slow startup of your PC, but the cumulative result of all. You might check the startup list and realize that you do need them all. But you may not need them all to begin at the same time when you want to check email in Outlook or do a report in a hurry.
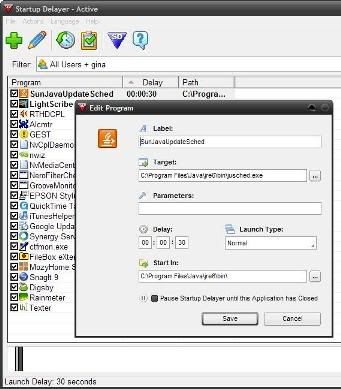
Application Startup Delayer can delay the process of "startup" applications ranging from 20 seconds, several minutes, even to the unit of hours so you can start to work while your PC to start all the startup programs gradually. If for example we do not need the Java Updater to start every time the PC is turned on, we can delay the startup of this program a few minutes after the PC boots.
Ccleaner and SystemExplorer addition, there's more like alternati MZ Ultimate Tweaker and RegToy. Defer Application Startup Process
Surely not just one program only result in slow startup of your PC, but the cumulative result of all. You might check the startup list and realize that you do need them all. But you may not need them all to begin at the same time when you want to check email in Outlook or do a report in a hurry.
Application Startup Delayer can delay the process of "startup" applications ranging from 20 seconds, several minutes, even to the unit of hours so you can start to work while your PC to start all the startup programs gradually. If for example we do not need the Java Updater to start every time the PC is turned on, we can delay the startup of this program a few minutes after the PC boots.
Do not Believe the Myths
Lots of myths, misperceptions and instructions on how to speed up the PC boot process in circulation. You must be careful in sorting it out. If you learn more about online tips for optimizing Windows, you'll find a way of deleting paging gile, clean the registry, set to use the PC core manually and many other tips. Before you do, try to first check a very interesting article about the myth of optimization of Windows Lifehacker.